Enhance Your Security with Our Comprehensive Source Code Review
Lynxes Source Code Review - Precision and Security Combined
Our Source Code Review involves a thorough examination of your application's code to identify any security vulnerabilities or backdoors. This process allows us to find and address potential weaknesses before they can be exploited.
Unlike traditional application tests, our comprehensive Source Code Review digs deeper into the software's design. This approach uncovers vulnerabilities that might otherwise go unnoticed.
We specifically look for issues such as injection flaws, cross-site scripting, CSRF vulnerabilities, and problems with authentication and session management in custom and proprietary code.
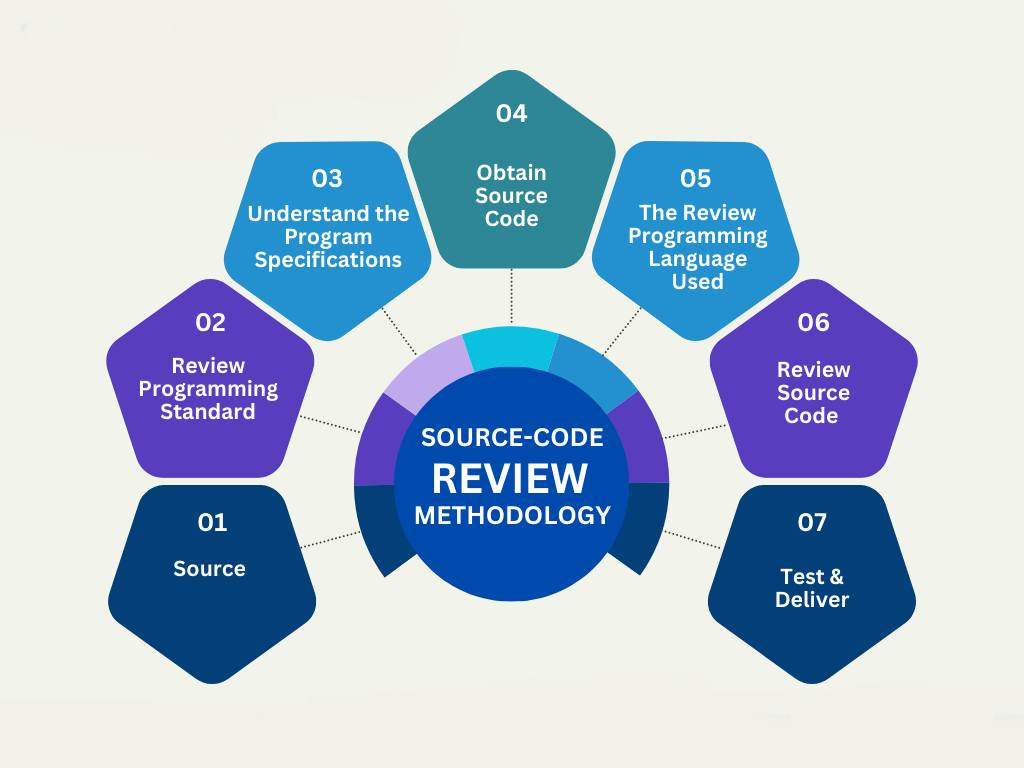
Why is Source Code Review Necessary?
Modern applications come with numerous features that provide users with easy access to business logic and data. However, if vulnerabilities are introduced, they can spread throughout the application, potentially halting your business operations. Additionally, understanding and securing IoT devices is crucial, as compromised devices can disrupt entire networks by being used in botnets.
Our Approach
We ensure that experienced consultants with relevant programming expertise handle your project. These experts use their extensive security knowledge to perform the review.
Preparation: In this phase, we review the application and create a threat assessment plan.
Code Review: We offer three methods: automated, manual, or a combination of both.
Automated Review: We use automated tools to check the code sequences, generate outputs, and compare them with the expected results.
Manual Review: Our experts examine the code manually for errors, insecure cryptographic practices, and platform-specific issues to identify logical flaws.
Reporting: After gathering all assessment data, we provide a clear, detailed report. This report includes criticality levels, risk assessments, technical and business impacts, and remediation strategies for each identified vulnerability.
Our team of experts is ready to help you ensure your company meets industry standards and protects both your business and your customers.
At Lynxes Solutions, our Security Architecture Design & Review service identifies and addresses systemic security issues in your environment. Ideal for businesses aiming to maximize their security technology investments, this service evaluates your current needs and validates the effectiveness of existing deployments. The outcome is a detailed roadmap for remediating any identified security gaps.
Features
Build Trust Conducting a Security Architecture Design & Review helps maintain and build trust with potential business partners and customers, which is crucial when competing for major contracts.
Network Segmentation Our review ensures effective network segmentation to prevent a single point of failure from compromising your entire infrastructure.
Enhanced Documentation We incorporate best practices to improve your network documentation, covering key components, segmentation, logging, policies, procedures, and a reliable network diagram.
Standardization Our review ensures standardization across your network, simplifying future audits and making it easier to address discrepancies.
When Should You Perform a Review?
- After experiencing a security breach.
- When planning a network redesign or expansion.
- If business expansion exceeds current network capacity.
- To gain better insights/data into your network environment.
- To reduce the burden of regulatory compliance (e.g., PCI, HIPAA).
- If you suspect vulnerabilities in your network infrastructure.
- To meet contract obligations with business partners and customers.
- After a merger or acquisition.
- Following significant changes to your network environment.
- After major upgrades to your network.
Results of Security Architecture Review
- LAN Architecture
- WAN and Remote-Access Architecture
- Wireless Architecture
- Security Operations
- Tools and Solutions
Our review methodology produces actionable results. You will receive detailed observations, identified deficiencies, and remediation recommendations covering:
Our review methodology is based on NIST (National Institute of Standards and Technology) and CIS (The Center for Internet Security) guidelines. By analyzing system documentation, configuration data, and interviews with key personnel, we assess your current security posture and provide actionable steps to address any identified gaps.
A firewall and network architecture review involves a thorough assessment of your firewall's effectiveness in protecting your systems, applications, and business operations. This review identifies vulnerabilities, assesses susceptibility to targeted attacks, and checks for misconfigurations that could compromise your security.
How Can a Firewall Security Review Benefit You?
Firewalls control network access and are essential for protecting against unauthorized access. However, configuring and updating them to meet changing business needs can introduce risks. A firewall review ensures that your security measures are up-to-date and effective, helping you comply with standards like PCI and HIPAA.
Lynxes Solutions' Firewall Security Review Services
Our Firewall Security Review Services are designed to enhance your security perimeter by identifying and addressing vulnerabilities. We cover all major firewalls, switches, and routers, and test for configuration issues, vulnerabilities, and compliance with industry standards such as PCI and HIPAA.
Using advanced tools and techniques, we identify security gaps and provide actionable recommendations for improvement.
Our team uses specialized tools to detect and resolve vulnerabilities, ensuring your firewall configurations are optimal and secure.
Client Benefits
- Our service provides trend analysis to enhance your security management and improve system protection.
- We offer independent verification of your firewall's effectiveness, leading to improved security in future projects.
- Benefit from our expertise to address security issues and enhance the performance of your firewalls and network devices.
- Our services help you meet regulatory requirements and standards, such as PCI DSS, ISO 27002, and HIPAA.
- Track engagement progress easily with our CC-GRC portal.
Service Frequency
Our Firewall Security Review Services can be performed as a standalone service or combined with other Lynxes Solutions services. Reviews can be scheduled regularly (e.g., quarterly or bi-annually) or in conjunction with major security updates. Services can be conducted remotely or on-site, with the option for clients to provide raw data for in-depth analysis.