Strengthening Cyber Resilience Through Proactive Testing and Strategic Solutions
Lynxes Solutions - Elevate Your Security Posture with Proven Penetration Testing Excellence
At Lynxes Solutions, we provide thorough vulnerability assessment and penetration testing services to keep your organization’s data and systems secure. Our security experts will collaborate with you to identify potential vulnerabilities and suggest effective solutions to mitigate risks. We also conduct penetration testing to simulate real-world attacks, assessing your organization’s ability to detect and respond to threats.
Our team of experienced professionals will tailor a testing plan to your specific environment and business needs, ensuring that all critical aspects of your security posture are evaluated.
We offer a range of testing services including black box, white box, social engineering, and physical security assessments. This comprehensive approach ensures we identify any potential vulnerabilities that could compromise your organization's security.
Don’t wait until it's too late—contact Lynxes Solutions today to learn more about our penetration testing services and how we can enhance your business's security.
Ethical Hacking to Prevent Potential Intrusions
Lynxes Solutions offers comprehensive penetration testing services to uncover system vulnerabilities, validate existing security measures, and provide a detailed remediation roadmap.
Our team, equipped with the latest tools and industry-specific test scenarios, conducts thorough checks to identify vulnerabilities in systems, applications, services, OS, configurations, and compliance with security policies.
Types of Penetration Testing We Provide
- Network Services Testing
- Web Application Penetration Testing
- Physical Security Testing
- Remote Access Security Testing
- Social Engineering Testing
Penetration Testing Process
Deliverables
Upon completing the penetration testing, we provide detailed reports and actionable recommendations to address identified vulnerabilities:
- Summary of findings and achieved results.
- List of detected vulnerabilities, classified by ease of exploitation and potential impact.
- Summary of changes made during testing.
- Test protocol, including tools used, parts tested, and issues found.
- Actionable recommendations to address revealed security issues.
At Lynxes Solutions, we perform Mobile Penetration Testing to simulate potential security breaches targeting custom mobile applications (iOS and Android). Our goal is to identify vulnerabilities that could lead to data loss and compromise your application’s integrity.
Our skilled penetration testers thoroughly examine the traffic between the mobile application and its API. We scrutinize request structures, modify fields, and intercept data to ensure your application's security against potential threats.

For the mobile application, we test:
- Data storage
- Network communication (API interaction)
- Platform interaction – local identification
- Security configurations (signatures, debugging)
For the API and server, we test:
- All functionalities
- Server services (web, mail, FTP, SSH)
- Security configurations of each component
- Use of third-party components
We document our findings meticulously, providing a detailed report of tested areas, identified vulnerabilities, and remediation recommendations. This report aids developers in addressing and fixing any discovered issues.
The report includes:
- Identified flaws
- Locations of flaws
- Descriptions of flaws
- Implications of flaws and potential exploitation
- Exploitation details during testing
- Remediation recommendations
Vulnerabilities are rated based on their likelihood and impact. Our professional team focuses on addressing critical vulnerabilities to enhance your mobile application’s security.
Common Mobile Penetration Testing Vulnerabilities:
- Improper Platform Usage
- Insecure Data Storage
- Insecure Communication
- Insecure Authentication
- Insufficient Cryptography
- Insecure Authorization
- Client Code Quality
- Code Tampering
- Reverse Engineering
- Extraneous Functionality
Benefits of Mobile Penetration Testing
- Enhanced Security: Identify and fix vulnerabilities to prevent unauthorized access and data breaches.
- Compliance: Meet industry regulations and standards for mobile application security.
- Improved User Trust: Ensure users’ data is protected, enhancing their confidence in your app.
- Risk Management: Identify and mitigate risks before they can be exploited by malicious actors.
- Continuous Improvement: Regular testing helps maintain and improve security over time.
Mobile Penetration Testing is an essential component of a robust security strategy. By identifying and addressing potential vulnerabilities, we help ensure that your mobile applications remain secure and resilient against emerging threats.
Network Penetration Testing is designed to uncover vulnerabilities in your network systems and applications. By using a range of techniques, we assess the security of your network, identifying potential weaknesses before malicious actors can exploit them.
This in-depth evaluation helps businesses understand their network's baseline, test security controls, prevent breaches, and ensure future security. It's especially beneficial for businesses with mature security postures or those believing their defenses are robust.
Our comprehensive penetration testing includes:
Step 1: Information Gathering and Client Expectations
Step 2: Reconnaissance and Discovery
Step 3: Performing the Network Penetration Test
Step 4: Reporting, Recommendations, and Remediation
-
We offer both Black Box and White Box testing services. Our approach ensures that we uncover vulnerabilities that could compromise your organization’s security.
- Black Box Testing
- White Box Testing
Black Box Testing
This type of test simulates an attack from an external hacker with minimal internal knowledge. It’s typically the quickest method, focusing on identifying and exploiting vulnerabilities in outward-facing networks.
White Box Testing
White Box Testing provides a more thorough analysis by having full knowledge of the network's internal workings. This approach allows for a deeper evaluation of your security controls and potential vulnerabilities.
- Understanding your network baseline
- Testing your security posture and controls
- Preventing network and data breaches
- Ensuring comprehensive network and system security
Benefits of Network Penetration Testing
API Penetration Testing involves ethical hacking to evaluate the security of your API design. Our process includes attempting to exploit identified vulnerabilities and providing recommendations to strengthen your API, safeguarding it from unauthorized access and potential data breaches.
Our comprehensive API penetration testing services ensure that your API endpoints adhere to best practices. We provide detailed analysis to verify that your APIs are securely supporting your web and mobile applications. This testing reveals how vulnerabilities could impact your business, including effects on the Confidentiality, Availability, and Integrity of your systems. Our reports help you prioritize vulnerabilities for immediate remediation and optimize your budget for enhanced cybersecurity resilience.
Our approach combines both manual and automated testing. While automated tests are efficient, we believe that thorough manual testing is essential for a comprehensive evaluation. At Lynxes Solutions, we employ rigorous manual techniques to ensure the effectiveness and completeness of our penetration tests.
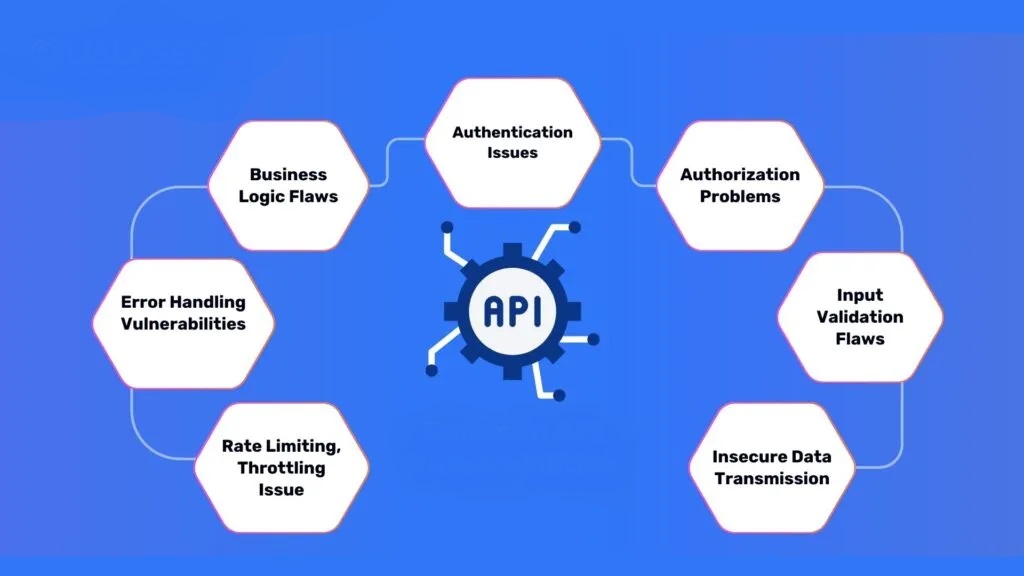
Benefits of API Penetration Testing
- API testing verifies the security of your methods and data. Our expert team ensures that business logic remains intact while safely transferring data between applications and databases.
- Regular API updates and frequent testing help maintain reliable performance and avoid costly remediation.
- Enhanced API security reduces the risk of data exfiltration and application compromise.
Web application penetration testing involves simulating attacks on your web applications to assess their security. The goal is to identify vulnerabilities and weaknesses that could be exploited by malicious actors. This process helps determine if your applications are secure, uncover potential risks, and ensure that effective security measures are in place.
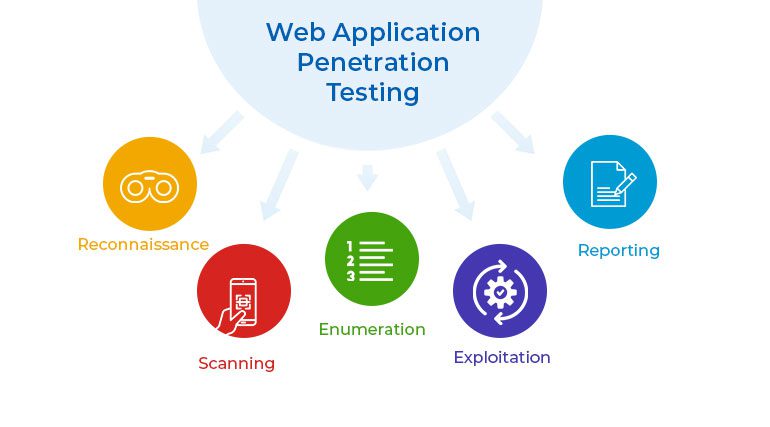
Our penetration testing follows a structured approach to ensure comprehensive security assessments:
1) Planning Phase
In the planning phase, we outline the scope, timeline, and objectives of the testing. We define the target environment and establish communication protocols. This phase ensures that we address both internal and external testing needs within a defined timeframe to enhance your application's security posture.
2) Pre-Attack Phase
This phase involves reconnaissance to gather information that will guide the subsequent testing phases. We perform tasks such as port scanning and vulnerability assessment to identify potential security weaknesses.
3) Attack Phase
During the attack phase, we conduct vulnerability detection and exploitation based on the findings from the previous phase. Our goal is to simulate real-world attacks to assess the effectiveness of your security measures.
4) Post-Attack Phase
After completing the testing, we provide a detailed report outlining vulnerabilities, analysis, and recommended actions. This report includes a comprehensive overview of our findings and suggestions for enhancing your security.
Benefits of Web Application Penetration Testing
- Meets compliance requirements where applicable, ensuring adherence to industry standards.
- Evaluates infrastructure by identifying potential vulnerabilities in public-facing systems.
- Identifies critical vulnerabilities that could be exploited, helping to strengthen application security.
- Validates security policies by assessing their effectiveness against potential threats.
Incorporating web application penetration testing into your security strategy offers several key benefits:
Deliverables
Upon completion of the penetration test, we provide a detailed report with actionable recommendations to address identified vulnerabilities:
- Summary of findings and achieved results.
- List of identified vulnerabilities, categorized by their severity and impact.
- Record of any changes made during the testing process.
- Testing protocol, including tools and methodologies used.
- Practical recommendations for mitigating identified security issues.
At Lynxes Solutions, our Red Team experts simulate real-world attacks to test and enhance your organization’s security. By identifying vulnerabilities and exploiting them in a controlled environment, we provide valuable insights into your defense mechanisms. This proactive approach allows us to collaborate with your internal teams to strengthen your overall security posture.
Our seasoned Red Team professionals bring extensive experience to the table. They focus on creating realistic attack scenarios, using cutting-edge tools, and maintaining clear objectives to ensure effective and thorough testing. We aim to uncover weaknesses in your infrastructure, processes, and personnel to fortify your defenses.
Red Team testing, often referred to as “ethical hacking,” involves our team posing as attackers to evaluate your organization’s security vulnerabilities. This process helps gauge how well your defenses stand up to real threats, providing a clear picture of your security readiness.

Our Red Team exercises target not only your technical infrastructure but also human and physical factors. We employ various techniques, including social engineering, phishing simulations, and penetration tests, to identify and address potential security gaps.
The process begins with a comprehensive reconnaissance phase where we gather information about your network, systems, and potential vulnerabilities. This intelligence helps us craft an effective attack strategy and identify the most likely paths of exploitation.
- Define security roles and responsibilities within your organization.
- Maintain a risk-based security posture to ensure business continuity.
- Plan and execute remediation strategies effectively.
- Implement security controls based on the criticality and sensitivity of your data assets.
- Report information security incidents to relevant authorities.
Benefits of Red Team Engagement
- Identify attack vectors that could be exploited by malicious actors.
- Demonstrate potential attack paths and how an attacker might move through your system.
- Assess your organization’s ability to detect, prevent, and respond to advanced threats.
- Explore alternative outcomes and responses to potential attacks.
- Prioritize remediation efforts based on the highest risks.
- Build a compelling business case for security improvements and investments.
Deliverables
- We provide a detailed report on the results and technical findings from our Red Team exercises.
- A comprehensive list of identified vulnerabilities, categorized by exploitability and potential impact on your business.
At Lynxes Solutions, our Purple Team services offer a comprehensive approach to cybersecurity by integrating both offensive and defensive strategies. We act as a crucial link between Red and Blue Teams to ensure your organization's assets remain secure.
Our Purple Team functions as a feedback bridge, enhancing the effectiveness of Red and Blue Teams. By facilitating the exchange of intelligence and real-time feedback, we help improve your overall security posture.
Best Practices for Implementing a Purple Team
To maximize the benefits of our Purple Team services, consider the following best practices:
Define Clear Roles
Effective collaboration and communication are essential. Ensure that each team’s roles and responsibilities are well-defined. Avoid expecting Red Team members to handle the full vulnerability management process, and don’t hold Blue Team members to the same expectations as expert hackers.
Prioritize Planning
Clearly define your goals to get the most out of the Purple Team exercise. Whether improving security alerts, refining policies, or assessing employee defenses against social engineering, thorough planning is crucial.
Track and Revise
Before implementing security improvements, meticulously track and review each step. Assess each task carefully before proceeding and always follow up to ensure thoroughness.
Benefits of a Purple Team
- Enhanced vulnerability detection capabilities
- Foster a stronger cybersecurity culture by integrating Red and Blue Teams
- Improved security design and exercise effectiveness
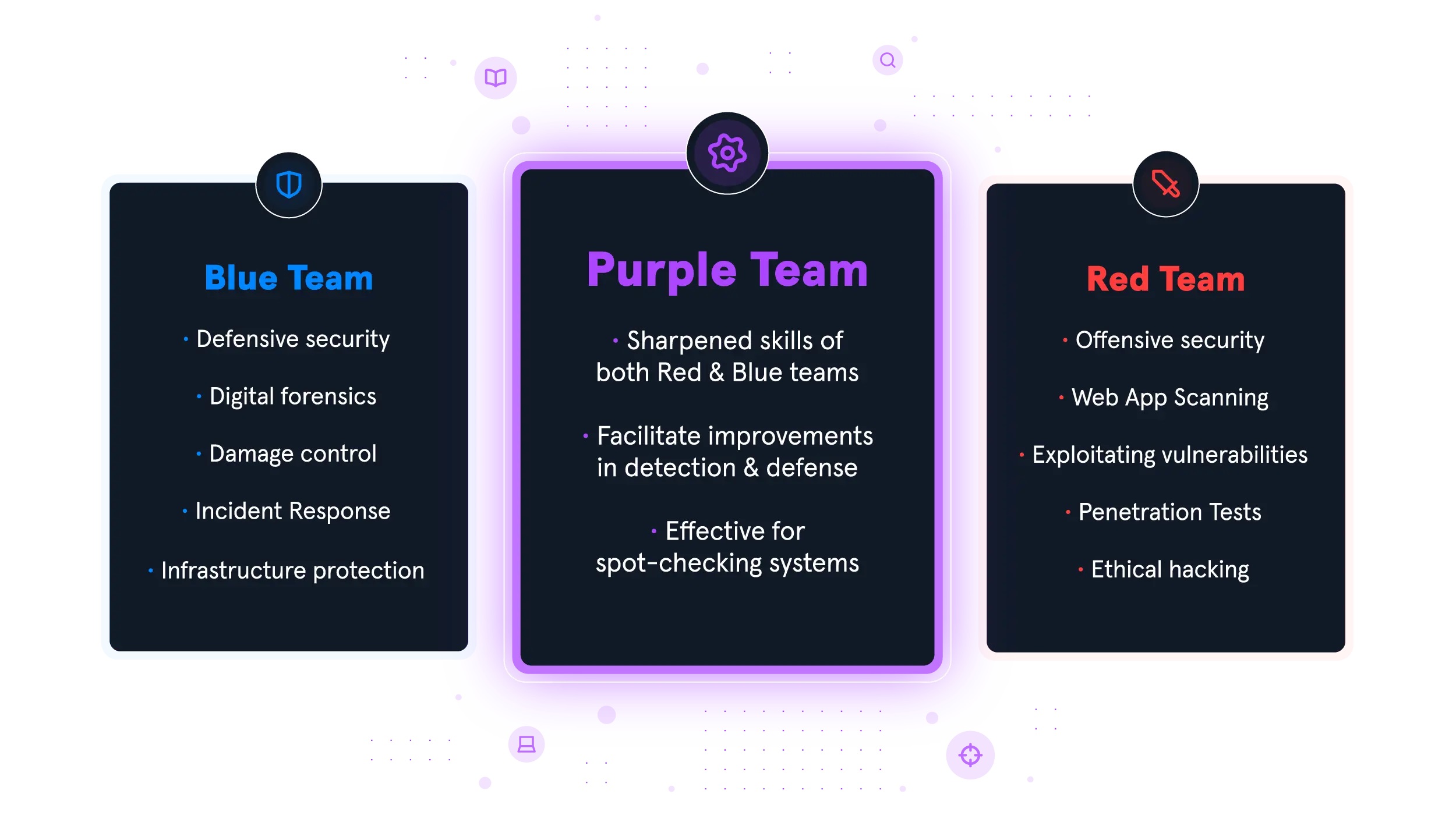
Our expert Purple Team members are highly trained and experienced, consistently delivering successful outcomes for our clients.
Wireless Security Testing is essential for evaluating the configuration and deployment of your wireless networks and devices. Our goal is to ensure that only authorized users can access your network and its services.
We conduct thorough wireless assessments using advanced signal scanning and configuration reviews of your wireless infrastructure. This helps us identify and address vulnerabilities specific to your setup. Because each testing scenario is unique, we provide bespoke solutions rather than fixed-price options.

We will scope your project requirements carefully, estimate the time required, and provide a detailed proposal with a breakdown of costs and options.
Our experienced team brings years of expertise in both government and commercial environments, always going the extra mile to meet your needs.
The Strategies and Tools of Wireless Security TestingOur wireless security experts perform a comprehensive range of tests on your Wireless Local Area Network (WLAN) and Wireless Access Points (WAPs).
Our wireless penetration testing aims to achieve:
- Evaluate the effectiveness of your wireless security programs
- Assess the risks associated with each wireless access point
- Identify and evaluate vulnerabilities
- Create a data-driven action plan to address vulnerabilities and mitigate risks
Wireless Security Testing Methodology
Our methodology for wireless testing consists of five key phases, conducted meticulously to identify and rectify security gaps.
Information GatheringThis phase involves network enumeration and identifying the SSIDs (network names) within the range of your Wi-Fi network.
Threat ModelingWe use the information gathered to model potential threats, categorizing assets into various threat categories.
Vulnerability AnalysisDuring this step, we review, document, and analyze vulnerabilities identified through previous phases.
ExploitationIn the exploitation phase, we attempt to gain access to your wireless network and potentially your internal network by bypassing security controls and exploiting vulnerabilities to assess their real-world impact.
ReportingWe provide a comprehensive report with actionable results, documenting findings, risk ratings, and evidence to guide remediation efforts.
 Benefits of Wireless Security Testing
Benefits of Wireless Security Testing
Wireless Security Testing offers assurance by addressing: - Access Control: Ensuring your wireless network is protected from external access. - Network Separation: Preventing guest or public hotspot users from accessing internal networks. - Configuration Security: Verifying that access points, controllers, and devices are securely configured. - Deployment Integrity: Ensuring that only authorized access points are installed, with no rogue devices present.
DeliverablesOur deliverables include: - Executive Summary: A non-technical overview for management. - Detailed Findings: A complete list of identified issues. - Affected Hosts: A list of all affected wireless hosts/SSIDs/configuration settings. - Risk Levels: Clear impact, likelihood, and risk ratings for each issue. - Examples: Screenshots or outputs demonstrating issues. - Recommendations: Guidance on how to remediate identified issues.