Assessments
Ensuring Compliance and Security Measures
Data privacy involves protecting personal information by controlling who can access and use it. It's essential for safeguarding individuals and organizations from identity theft, fraud, and abuse.
Organizations need to protect their employees' and customers' personal information. A data privacy assessment helps evaluate how well an organization is safeguarding this information.
Common data privacy regulations include the General Data Protection Regulation (GDPR), Health Insurance Portability and Accountability Act (HIPAA), and Payment Card Industry Data Security Standard (PCI DSS). Adhering to these regulations is crucial for protecting personal information.
Steps for a data privacy assessment include understanding applicable regulations, identifying collected personal information, assessing protection measures, and reviewing the incident response plan.
The Lynxes Solutions team of certified consultants can assist with data privacy assessments, leveraging our expertise with GDPR, HIPAA, and PCI DSS to enhance your security measures.
Threat vulnerability and risk assessments identify, quantify, and manage risks to information resources. The goal is to protect your organization’s information and stakeholders from potential threats.
The assessment process includes identifying threats, estimating their impact, evaluating current controls, and recommending additional protective measures if needed.
Various methodologies, such as NIST Special Publication 800-30, ISO/IEC 27005, and COBIT 5, offer different strengths. Choose the one that best fits your organization’s needs.
- Assessment
- Response
- Monitoring
The three phases of information security risk management are:
The Lynxes Solutions team is ready to help with threat and risk assessments. Our experts use the latest tools and techniques to ensure comprehensive protection for your organization.
A compromise assessment helps identify and manage risks associated with potential cyber-attacks. The goal is to provide insights for better protection of systems and data.
Types of assessments include technical and non-technical approaches. Technical assessments focus on system configurations and security controls, while non-technical ones address organizational and managerial factors.
- Technical
- Non-Technical
Types of compromise assessments include:
Lynxes Solutions offers comprehensive compromise assessments to help identify risks and prepare for potential incidents. We provide expert advice and support to safeguard your organization.
A cloud security assessment evaluates the security of your cloud environment. This includes reviewing your cloud provider’s security measures, assessing how your organization integrates with the cloud, and understanding how the cloud will be utilized.
Whether you're considering moving to the cloud or already using cloud services, these assessments help identify potential risks and vulnerabilities. They also aid in developing strategies to mitigate these risks effectively.
- Moving data or applications to the cloud
- Implementing new cloud features or functionality
- Switching cloud providers
- Adding new users or groups to your cloud environment
Key phases in managing cloud security risks include:
Assessments can be done by internal teams or external experts. When choosing an assessor, consider their experience, expertise, and understanding of your security requirements. Post-assessment, review the findings and develop a plan to address any identified risks. Regular updates to this plan are crucial for maintaining effective cloud security.
Lynxes Solutions can assist in identifying and assessing your cloud security threats. Contact us to learn more about our cloud security assessment services.
Vulnerability assessment involves systematically analyzing the security weaknesses in your computer networks, hardware, applications, and systems. It’s essential to perform these assessments to identify and mitigate risks early. Our experts provide thorough and efficient vulnerability assessments tailored to your needs.
A comprehensive vulnerability assessment identifies, prioritizes, and addresses weaknesses, providing you with a clear roadmap for remediation.
Lynxes Solutions offers complete vulnerability assessment services, including identifying system vulnerabilities, validating existing security measures, and providing detailed remediation plans.
- Defining and planning the scope of testing
- Identifying sensitive data locations
- Uncovering hidden data sources
- Identifying mission-critical applications
- Assessing network and system access points
- Reviewing ports, processes, and configurations
- Mapping out IT infrastructure and digital assets
Our assessment process includes:
1. Defining and Planning: Scope and plan the assessment.
2. Vulnerability Identification: Conduct scans and manual tests to identify threats.
3. Analysis: Analyze findings, prioritize vulnerabilities based on risk, and create a remediation plan.
4. Remediation: Implement fixes based on the remediation plan to address vulnerabilities and prevent exploitation.
For thorough vulnerability assessments and effective remediation, contact Lynxes Solutions today.
Social engineering assessments test how well your employees handle security threats. These tests simulate real-life scenarios where attackers exploit common human traits like trust and emotional responses to gain unauthorized access or sensitive information.
Our assessments use psychological tactics to trick individuals into performing actions like clicking on fake links, opening harmful attachments, or sharing confidential details. This helps us understand how your team responds to such manipulative techniques and how well your current security measures hold up.
The impact of a successful social engineering attack can be severe, compromising critical business data, employee information, and more.
Lynxes Solutions' Social Engineering services evaluate how well your systems and personnel detect and respond to these attacks. We plan the tests carefully in coordination with you to ensure they're controlled and insightful. Our assessments help identify:
- Risks related to employee behavior that could lead to sensitive information leaks
- Understanding of your organization’s digital footprint and public information exposure
- Effectiveness of technical controls in detecting and responding to social engineering attacks
- Weaknesses in employee cybersecurity awareness
- Recommendations for improving human behavior and cybersecurity sensitivity
Our social engineering services include:
- Voice Phishing – Targeted phone-based social engineering campaigns
- SMS Phishing – Targeted SMS-based social engineering campaigns
- Tailgating – Gaining access to restricted areas by following employees
- Chat Phishing – Using messaging/chat services for social engineering
- Physical Bypass – Techniques to gain physical entry to secure areas
Our Methodology
Our social engineering assessment process includes:
- Information gathering and OSINT
- Target profiling and finalizing attack mode
- Launching the test
- Analyzing test results
- Reporting
Our Benchmarks
Our assessments meet the user awareness evaluation and training requirements for benchmarks like:
- ISO 27001:2013
- PCI-DSS
- Cybersecurity guidelines from regulatory authorities
Why Choose Us?
- Extensive experience conducting assessments across diverse industries, including BFSI, healthcare, IT, logistics, and more
- Highly trained experts providing a customized experience for each client
- Detailed reports offering insights into test results and business impacts
- Expertise in designing long-term awareness campaigns to improve information security culture
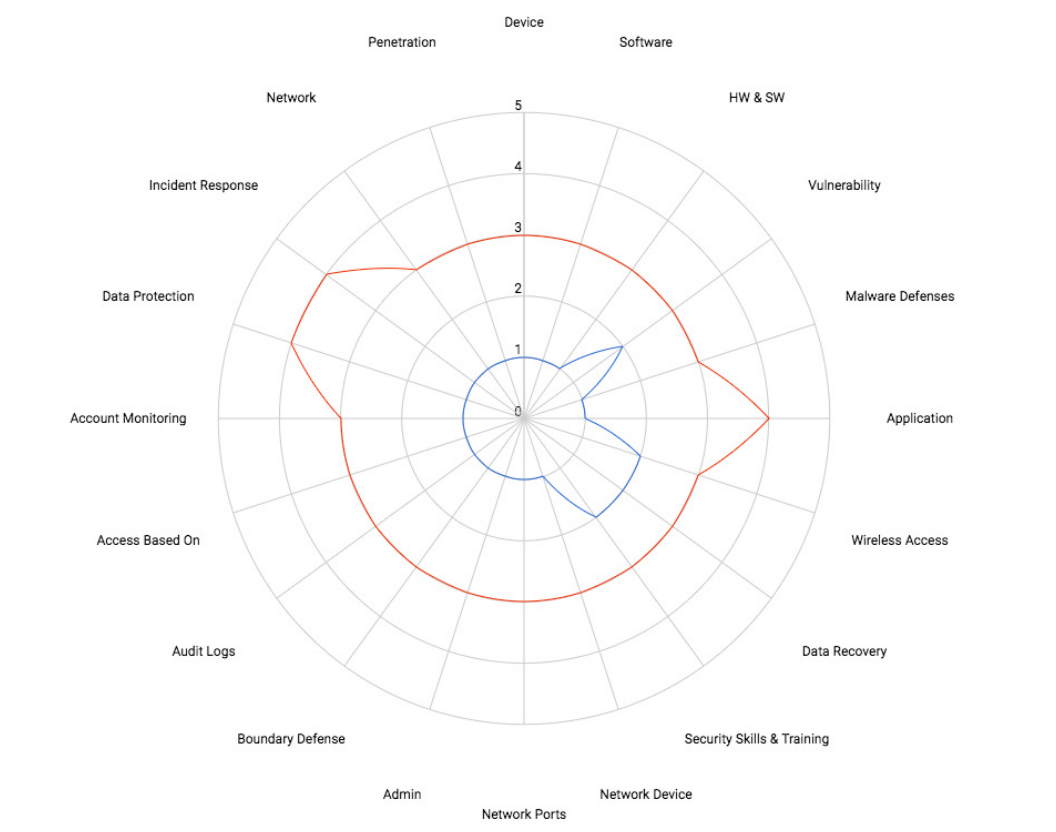
The Cyber Security Maturity Assessment (CSMA) provides a comprehensive view of your current security posture. It offers an objective review of existing plans and guides strategic planning to mature and strengthen your security efforts. Aligning your security program with the best practices outlined in this assessment enhances your ability to meet and exceed industry compliance standards.
HOW IT WORKS The CSMA evaluates specific controls that protect critical assets, infrastructure, applications, and data by assessing your organization's defensive posture. It highlights operational best practices for each control area and measures the effectiveness and maturity of internal policies and procedures.
The assessment also includes a review of compliance with various industry requirements and frameworks, including:
- Center for Internet Security Top 20 Common Security Controls (CSC20)
- NIST Cybersecurity Framework (NIST CSF)
- NIST Special Publication 800-53 (NIST 800-53)
- NIST Special Publication 800-171 (NIST 800-171)
- Department of Energy Cybersecurity Capability Maturity Model (DOE-C2M2)
- ISO/IEC 27001:2013 (ISO 27001)
These frameworks provide a structured approach to measure the maturity and effectiveness of your security program, both now and in the future.
The Capability Maturity Model
